Finalsemprojects based at Chennai providing services for final year engineering students from CSE, IT and ECE departments in their final year ieee project work in java ns2 python ieee project.
Final Year ieee projects Title / Topic List
Download ML/DL and AI IEEE Projects Ideas From Finalsemprojects
The above List contains Machine learning, deep learning, artificial intelligence project ideas for Computer science and IT students. Computer science and Engineering (CSE) students prefer software projects in Java, Python. Similarly, Information technology (IT) students also prefer the same.
We develop your Own Project Concepts also. Send your concepts to our email dataalcott@gmail.com
We guide on Phd implementations and paper writing.
Finalsemprojects
No 16/1,Kumaran Colony, First Street, Saidapet, Chennai-600015
Landmark: Near Aranganathan Subway
Contact : +91- 9600095046 / 47
Mail: dataalcott@gmail.com
DO YOU WANT ABSTRACT AND PPT? REQUEST US ON A CHAT NOW
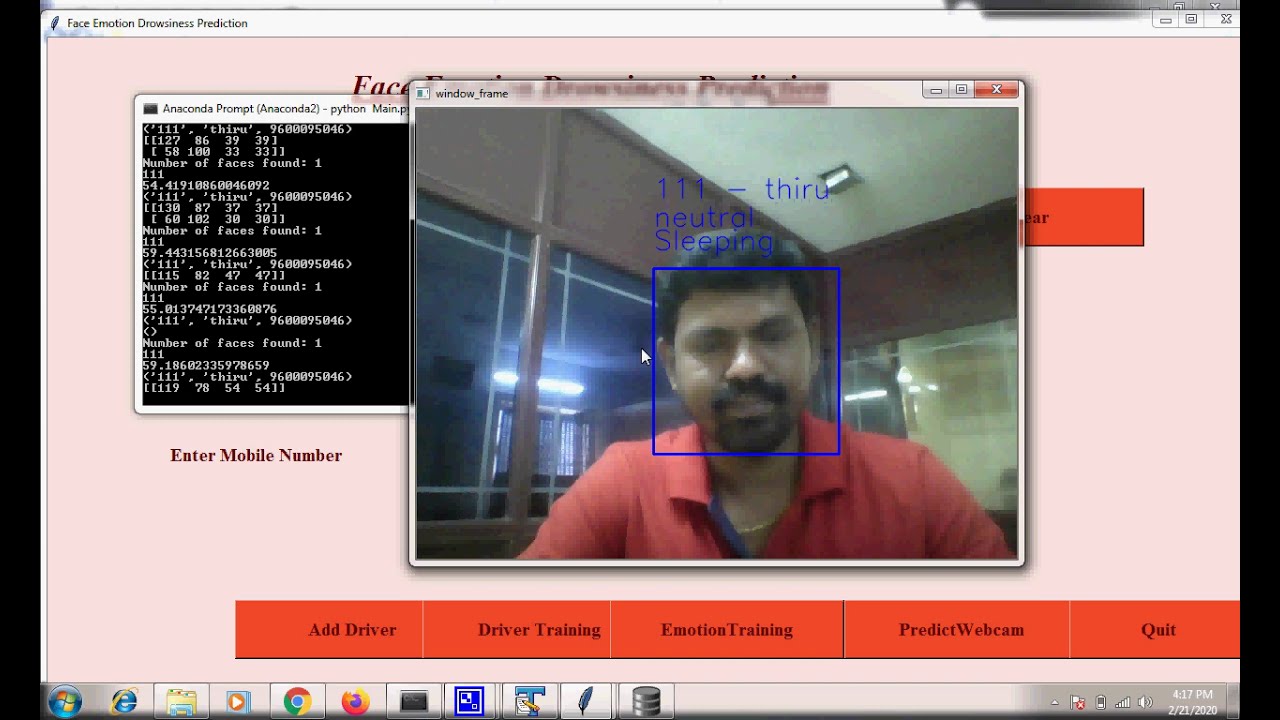
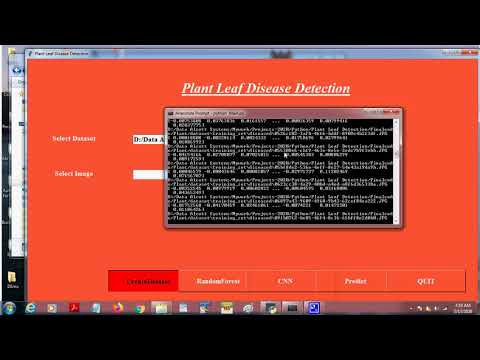
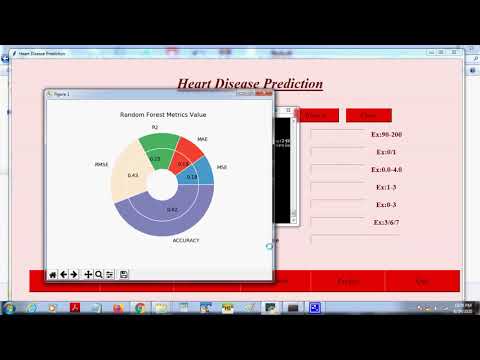
Want to check some of the projects output online? Please visit our Youtube Channel
What is IEEE projects?
IEEE is a standard Journal. Research scholars are publishing in all domain with IEEE. Students research scholars prefer to do novel concepts to publish it as journal.
Scopus Journal are also preferred for doing final year project by Engineering students in department Computer Science and Information Technology streams. We assists engineering students to complete their final semester projects at their best. We assist engineering students on Plagiarism free thesis writing.
Python Projects
Finalsemprojects also support Python implementation
Data science projects
Machine Learning projects
Deep Learning projects
Artificial Intelligence projects
We have wide range of projects in python programming. Top 100 Best Python projects ideas can be download in our website. Python projects in classification, regression are supported. Novel techniques such as hyper parameter tuning, hybrid algorithm in python projects are developed.
What We do?
We give engineering students project guidance for improving the already published paper. Novelty of the project or improvement in algorithm assistance are given. For engineering students, we try to cover as an application either in Widows or web based application to fulfill their completeness of project.
How we support?
Not during pandemic, we started our online journey more than 12 year back. We guide online around the world for engineering and Maters (MS) graduates and Research Scholars. Complete Support On Project Execution Through Remote Support Software will be provided.